Evil QR - Phishing With QR Codes
Evil QR is a spin-off of a QRLJacking attack, demonstrating how attackers could take over accounts by convincing users to scan supplied QR codes, through phishing.

Today I'm publishing the research I started to work on last year, but I was too busy with the Evilginx Mastery course, to publish it, at the time.
If you want a quick TL;DR rundown of what this blog post is about, check out the demo video I prepared:
Background
In recent years, I've noticed that more and more web applications begin to offer a new way to sign in - through QR code scanning. This method is especially convenient if you have a mobile app, on your phone, corresponding to the web application you are trying to sign into, in your web browser.
Here are the most popular websites, you can sign into, in any web browser, by scanning a QR code within the mobile application.
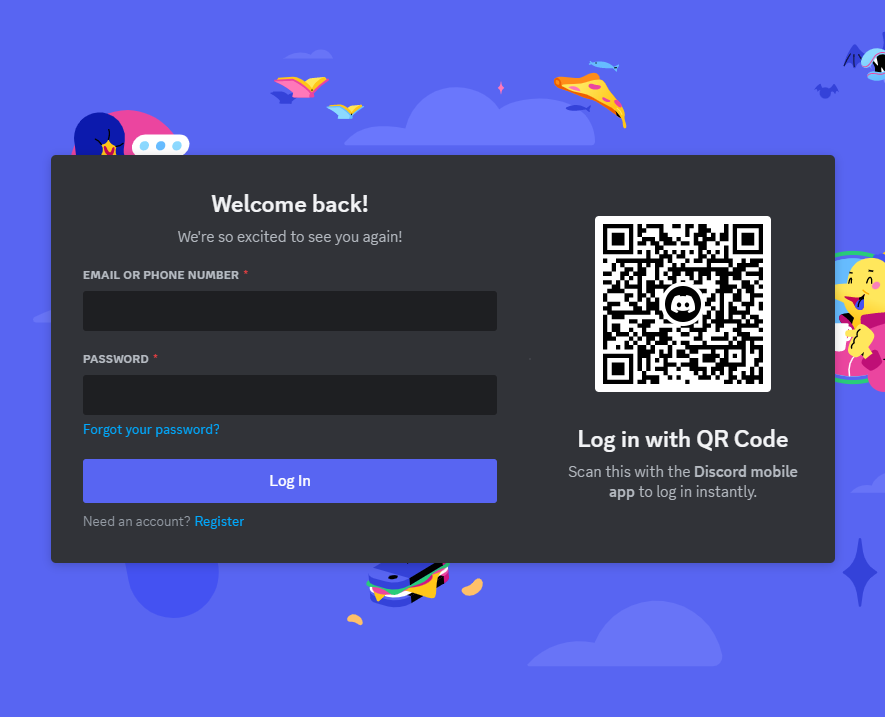
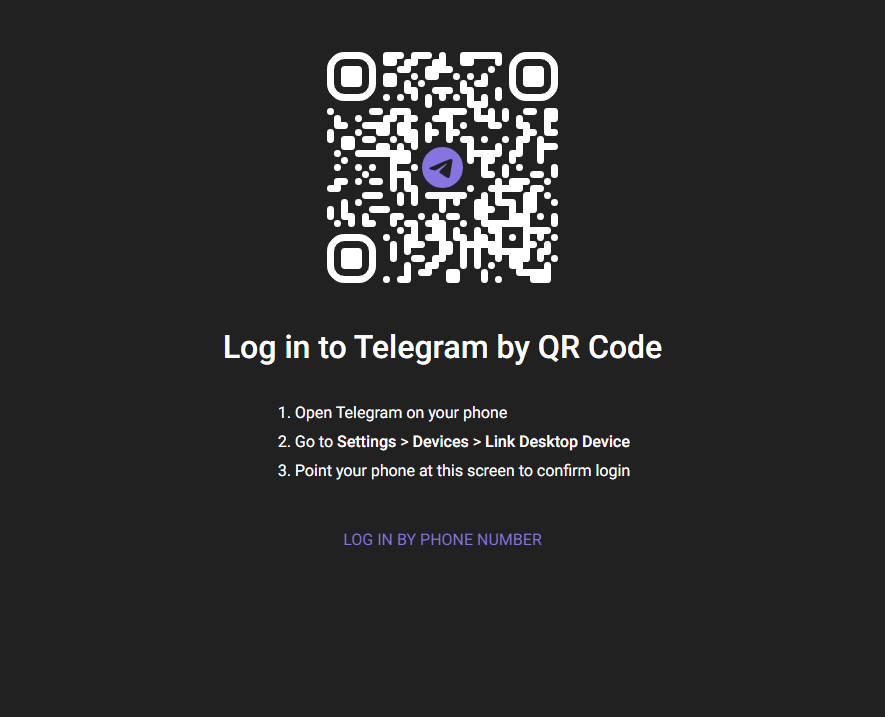
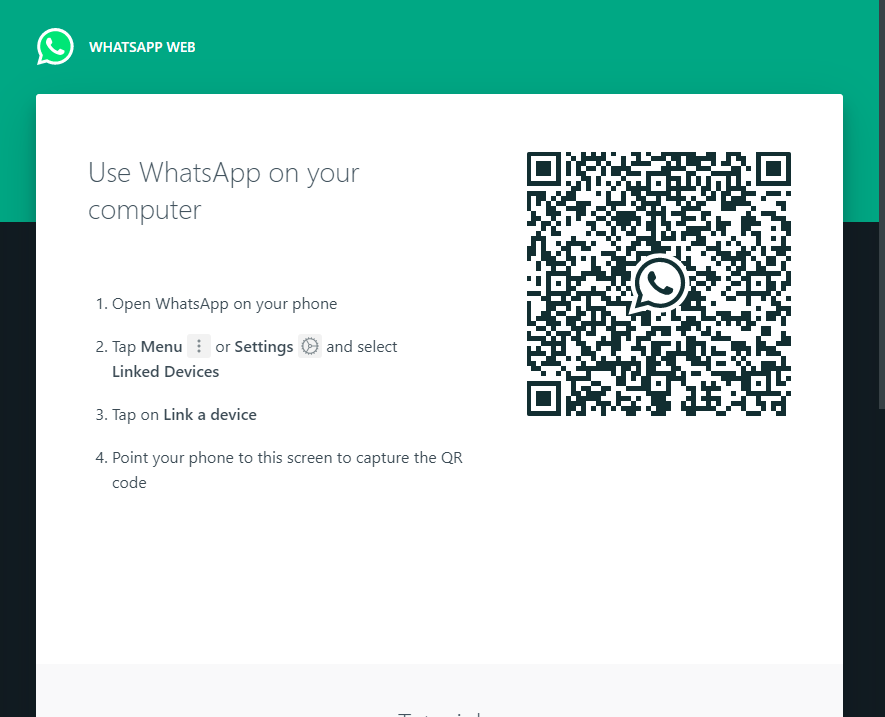
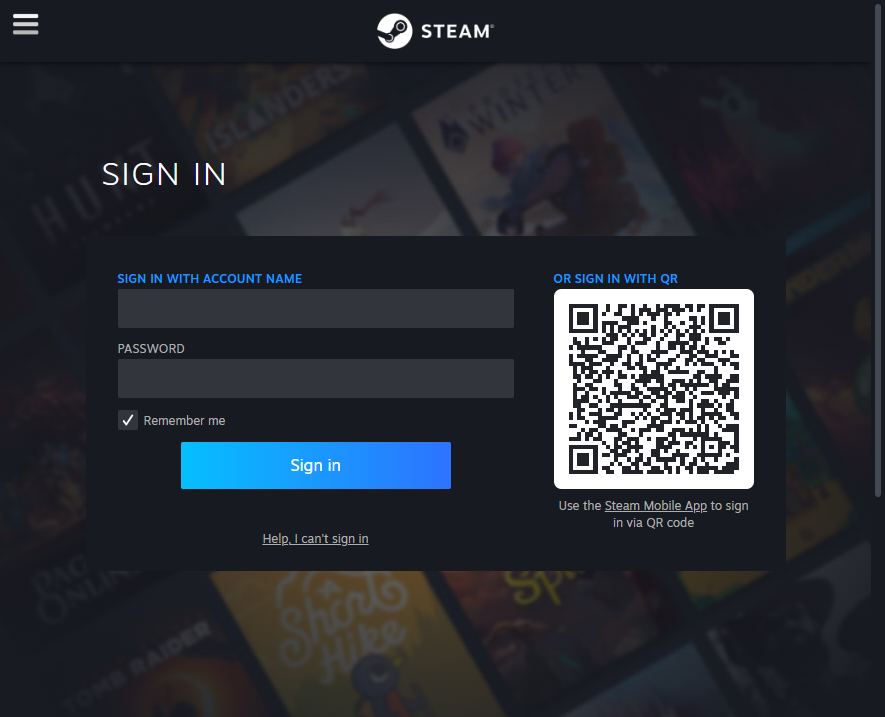
To sign in, you open the mobile application, navigate to "Scan QR code", usually residing somewhere within your profile settings, in the mobile application, and scan the QR with your phone camera.
The QR code, displayed on every sign-in page, is nothing more than a dynamically generated session token, which you can authorize with your mobile application, to pair it with your account.
Try to scan any of these QR codes with your phone's camera and you'll see the code translates into a unique string, usually presented in URL format. Here are several examples:
Discord:
https://discord.com/ra/GLt61XsN_fuakToqeSMV25pd3G-uwSbdScI1Zc9iwT8Whatsapp:
2@o7Ugs+XwUVXgG2f8stGluhiItwCxbZJNLkpkeKEhz65GmPh6+/N1lp3fXpaSjxeARrE2JGXi3ikIFA==,it98cjNOA3qvp4i/TidKTeWZTrGkFUTnqsOzPPxFEzI=,AMV+jQ0gSnoFFKbuYzKdrDSPT7BVZ4R5iFxIGEbCqQI=,nVAlyqnDJiYfW/S1LzZoaVNsDm+pNaB1mGm8pGC0+/E=,1Steam:
https://s.team/q/1/1711614348354244891TikTok:
https://www.tiktok.com/t/ZGJXCraU8/Binance:
https://www.binance.com/en/qr/93bd2ead7e504488bda81bf50deab7e8Now let's imagine if there is any potential way, attackers could convince users to scan the QR code with the session token they control.
Meet Evil QR Phishing aka QRLJacking
One day you receive an email, telling you that you've been granted exclusive access to a private Discord server, where highly valuable information will be shared, among the participants. All you need to do is open the attached link and scan the QR code with your Discord application.
You click the link and the following website shows up in your web browser:
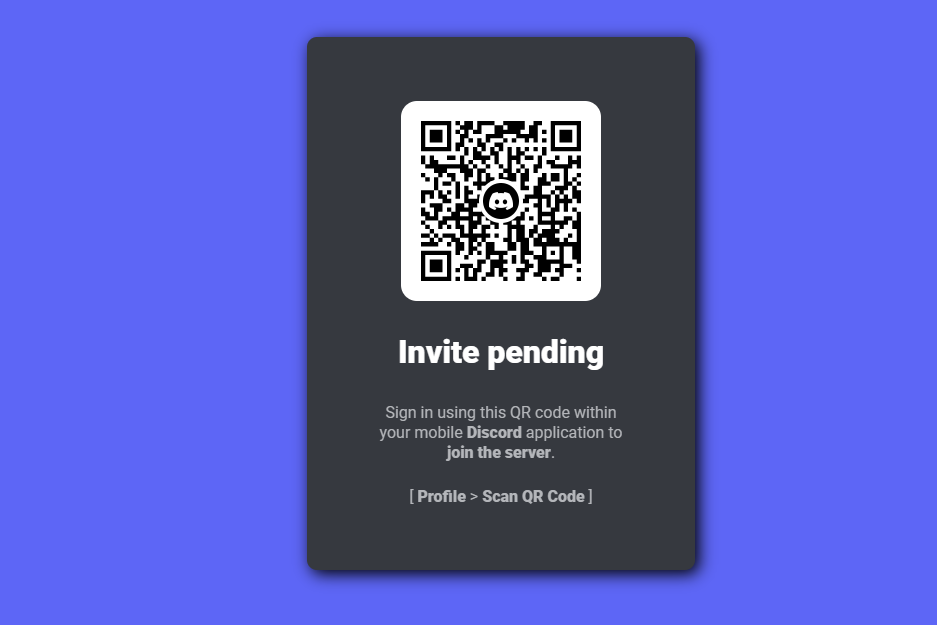
Since you are pretty excited to join, you open your Discord application and scan the QR code, showing up on the screen of your PC. Discord asks you to confirm if you want to sign in, using the scanned QR code. You think that it makes sense that you need to be signed in to join the Discord server, so you agree without hesitation.
Once you approve the login attempt, the website redirects you to the Discord server page. You lose interest and go back to your other activities. All this without realizing, you've just given the attacker full access to your account.
What happened?
Here is the step-by-step process of what the attacker did to pull off this phishing attack, using the Evil QR toolkit.
- The attacker opens the official Discord login page within their web browser to generate the sign-in QR code.
- Using the Evil QR browser extension, the attacker is able to extract the sign-in QR code from the login page and upload it to the Evil QR server, where the phishing page is hosted.
- The phishing page, hosted by the attacker, dynamically displays the most recent sign-in QR code controlled by the attacker.
Once the target successfully scans the QR code, the attacker takes over the phished account.
The concept of phishing users with sign-in QR codes is not new and it has been broadly documented by Mohamed Abdelbasset Elnouby (@SymbianSyMoh) from Seekurity in 2016! I highly recommend you read this post as it covers a lot of information about the potential attack vectors, which could be used to pull off such attacks.
The technique was later officially recognized as QRLJacking and @SymbianSyMoh also released a QRLJacker tool in 2020 to demonstrate how such attacks can be executed. Evil QR idea is just a spin-off of the same idea.
Evil QR Toolkit
To demonstrate this interesting phishing technique, I've developed a set of proof-of-concept tools for demonstration purposes.
You can find the open-sourced Evil QR toolkit on my GitHub if you're interested in trying it out yourself.
As you can see below, the Evil QR attack can be customized using personalized phishing pre-text, with dynamic updates, for every website separately. Evil QR browser extension can detect and extract QR codes, within websites, no matter how they are rendered.
The extension supports extracting QR codes rendered as CANVAS, IMG, SVG or even DIV (by taking a screenshot with html2canvas library).
Evil QR Server
The server is developed in GO and its main purpose is to expose REST API for the browser extension and run an HTTP server to host the phishing page.
It awaits authenticated communication from the browser extension including QR code image with metadata in JSON format on /qrcode/[qr_uuid] endpoint:
{
"id": "11111111-1111-1111-1111-111111111111",
"source": "data:image/png;base64,iVBORw0K...",
"host": "discord.com"
}The retrieved QR code is then stored and is available for retrieval by the JavaScript, running on the phishing page. The phishing page is using HTTP Long Polling to be able to retrieve QR code updates with minimal delays, without having to use Websockets.
The phishing page automatically detects which hostname the QR code was retrieved from and can dynamically adjust its CSS and text content to change the phishing pre-text, for social engineering purposes.
Evil QR Browser Extension
The extension is used solely by the attacker and it needs to be enabled on the sign-in page of the web application, the target is phished for. It will automatically find the QR code image and detect if it changes. Once it changes, it will upload the updated image to the Evil QR server.
One of the most important characteristics of session tokens represented by sign-in QR codes, is that the tokens are short-lived by design. Every token is made to expire approximately after 30 seconds, which drastically shortens the time frame of the token's validity. Once the token expires, the website regenerates it and updates the displayed QR code, on the sign-in page.
If the sign-in session tokens did not expire, the attackers would hypothetically be able to print out the QR codes on a physical piece of paper and send them as phishing leaflets to potential victims, since the tokens would never expire.
Some websites will stop updating QR codes, after a certain period of inactivity, to save bandwidth. When this happens, they will usually display a "Retry" button of some sort, which the extension can automatically detect and click on, to not interrupt the process of updating QR codes.
The extension can also detect the presence of a specific DOM object, which will show up only when the attacker is signed in after the phishing attempt is successful. It will then send an update to the Evil QR server with authorized: "true" parameter, allowing the phishing page to decide on how to proceed.
How serious is this?
In my personal opinion - not that serious. For the QRLJacking phishing attack to be successful, it requires a lot of prerequisites to be met prior to the attack taking place. Nevertheless, it was a very fun project to work on.
The classic phishing attacks, focused on capturing credentials and session tokens to bypass multi-factor authentication, are still much more dangerous than this one and they can be executed on a much larger scale using a tool like Evilginx for example.
I think the most realistic scenario of how QRLJacking phishing could be pulled off, would be to set up a phishing page with a QR code on display using an external device, deployed in public, like a tablet or TV screen. Once one person successfully signs in, by scanning a QR code, the attacker's Evil QR setup would save the captured session for later and reload the new sign-in page to generate a new QR code to phish another user.
That could in theory make it possible to phish a larger number of users, one at a time. I don't think QRLJacking phishing is a viable technique when sending phishing links via e-mail or other mediums. These days most people read incoming messages on their mobile phones and once the phishing page with a QR code shows up on their phone's screen, it is impossible to use the same phone's camera to scan it.
To summarize, here is a list of all pros and cons of executing this phishing attack technique, I could think of:
Pros:
- No need for the target to enter their username and password.
- Could be potentially pulled off in public areas, having an external device displaying a phishing QR code, on display.
Cons:
- Target needs to have the mobile app pre-installed for the given service.
- Attacks are hard to pull off, on a wider scale, since there has to be a separate QR code generated for every target.
- Usually pretty hard to find the setting to scan QR codes within mobile applications, involving multiple clicks, with every click lowering the chance of a successful social engineering attempt.
- If a phishing page is opened on a mobile phone, there is no way for the target to scan the QR code with the same mobile phone.
Closing thoughts
I decided not to implement this attack vector into Evilginx phishing framework, since Evilginx is already powerful on its own.
While sign-in QR codes displayed on phishing pages, reverse proxied by Evilginx, will not let you sign in by scanning them, due to hostname mismatch, it is still possible to patch the JavaScript code, which generates them, to make them work on phishing pages.
If you're interested in learning more about reverse proxy phishing to bypass MFA, check out my Evilginx Mastery video course, which will teach you everything you need to know to perform successful red team phishing engagements.
Till next time!